
Blog
Insights on graph theory, threat modeling, security architecture, and the economics of risk.
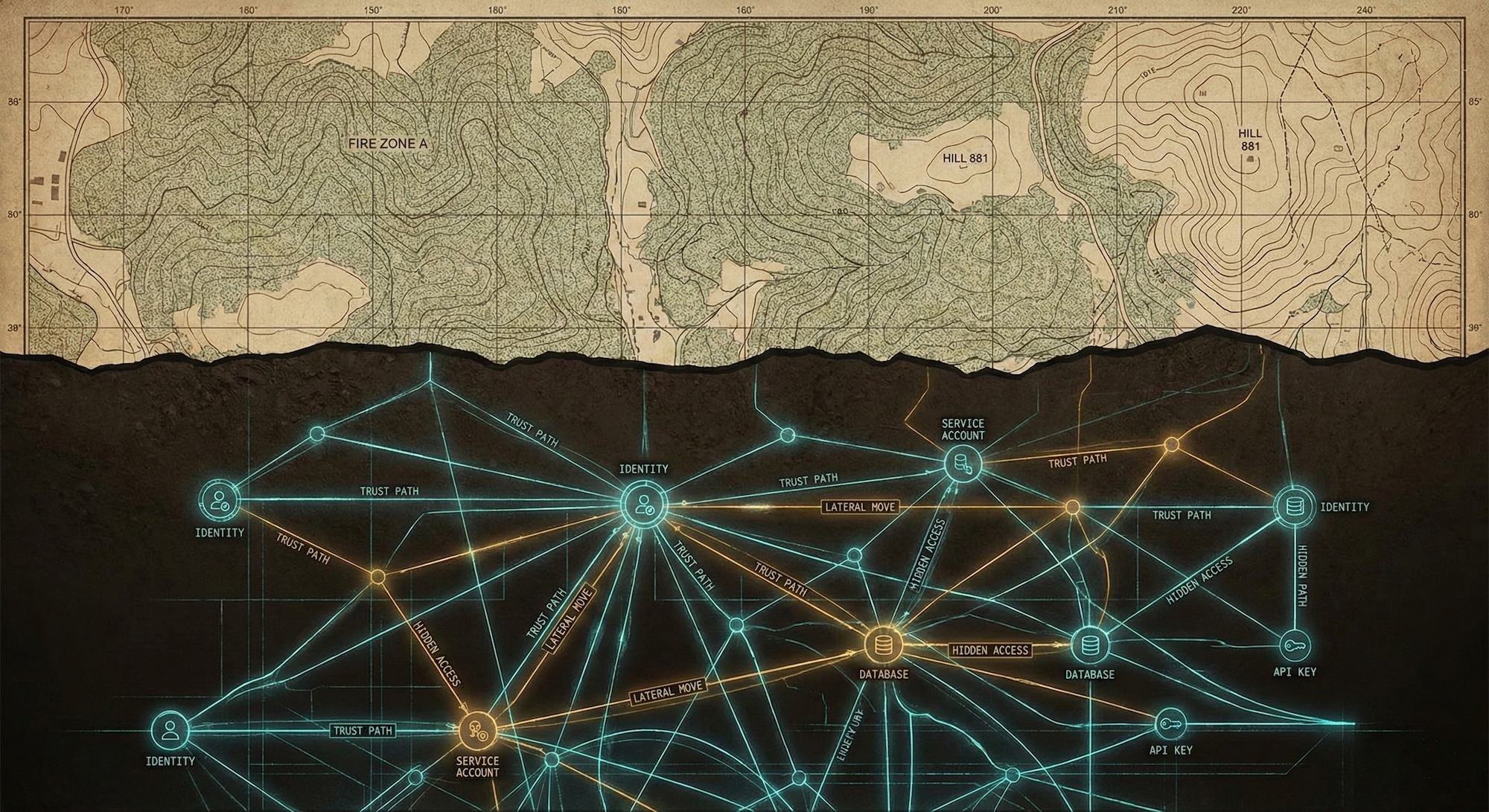
The Tunnels Under Your Security Boundaries
Every organization has two architectures: the one that was designed, and the one that actually exists. Drawing lessons from the Củ Chi tunnel network, this article examines why list-based security fails against graph-traversing adversaries.
February 4, 2026

Add the Firewall Last
When firewalls are your foundation, everything inside becomes one giant implicit trust zone. Design secure architecture first—nodes that can defend themselves—then add firewalls for defense in depth, not structural dependency.
February 2, 2026

Zero Trust Is Just Graph Theory with a Marketing Budget
Every vendor sells Zero Trust as an identity layer. But you can't remove implicit edges if you don't know what edges exist. Zero Trust is a topology change—and implementing it requires graph analysis, not just identity proxies.
January 23, 2026
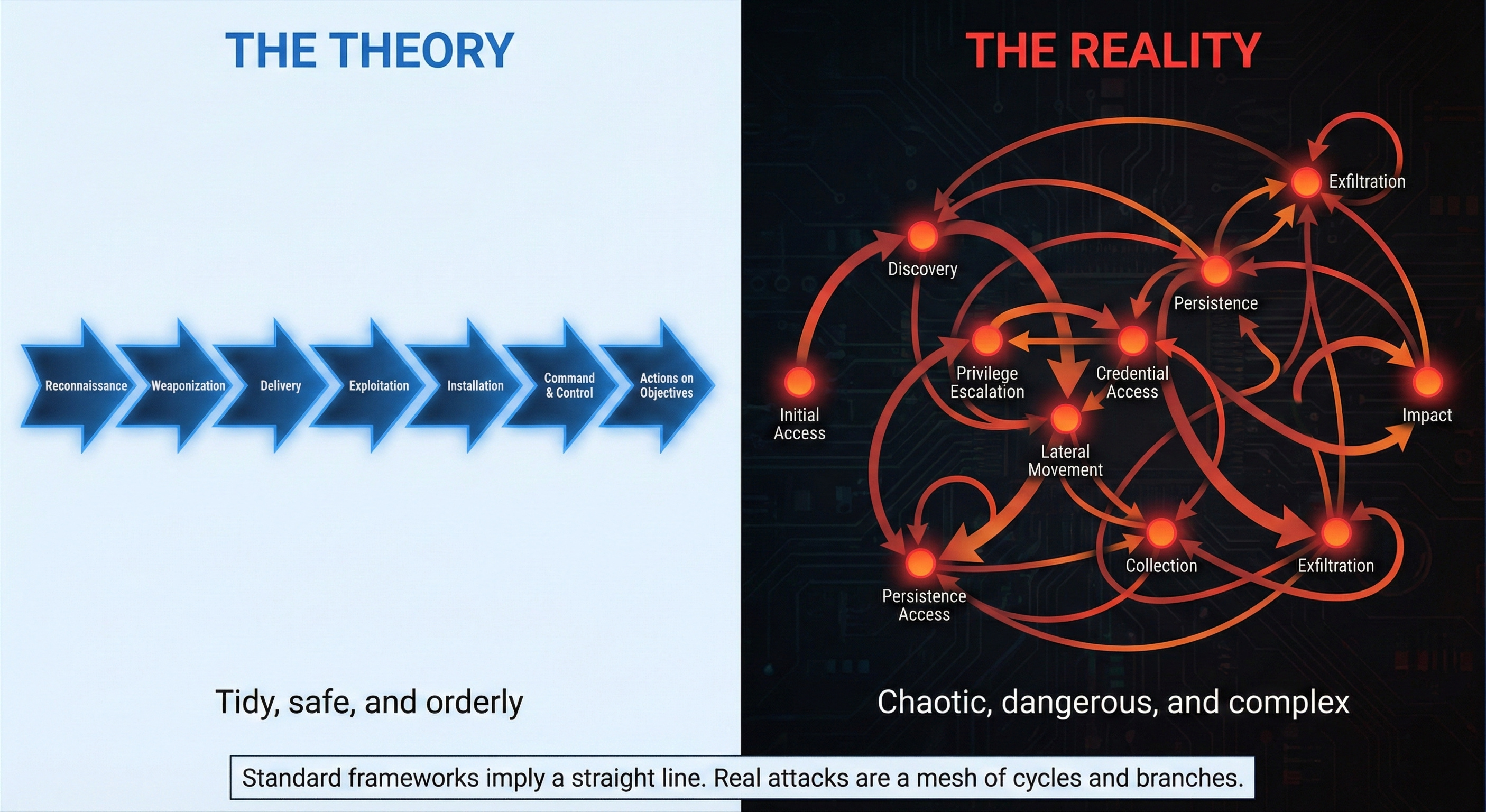
Attacks Are Graphs, Not Chains
The Kill Chain and MITRE ATT&CK model attacks as linear progressions. Real attacks loop through lateral movement cycles, branch based on objectives, and adapt to context. Graph theory reveals what linear models miss.
January 12, 2026

The Ephialtes Edge
The Spartans built the perfect chokepoint—and were destroyed by a path they didn't know existed. Your firewall faces the same math: security isn't about the strength of the gate, it's about knowing every edge in the graph.
January 8, 2026

Security Is a Graph Problem
Attack paths, blast radius, chokepoints—these aren't metaphors, they're graph algorithms. Learn why relational databases fail at security analysis and how graph-native thinking transforms architectural risk assessment.
December 29, 2025
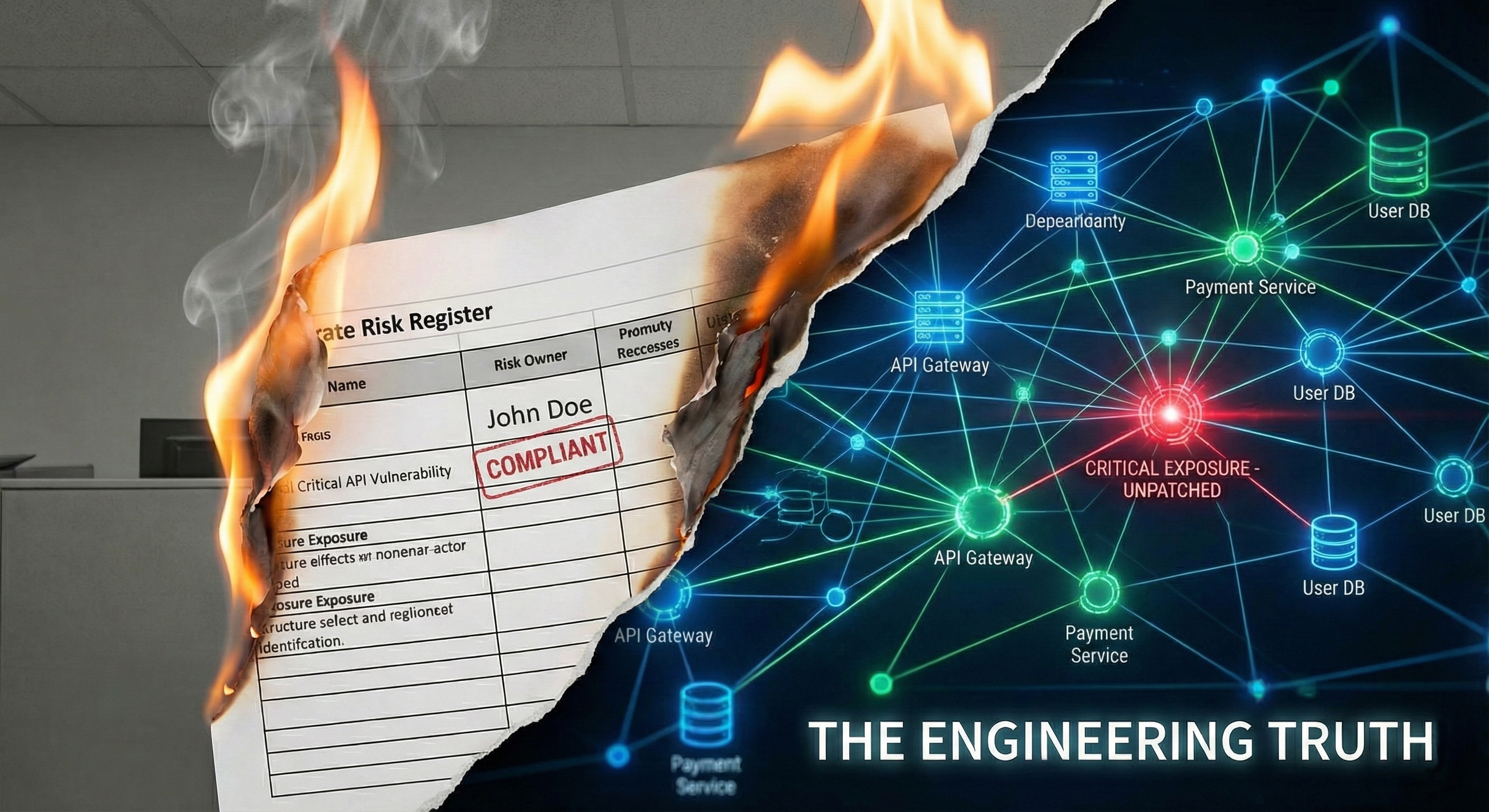
Why Risk Owners Never Fix Anything
Risk ownership is just a label in a spreadsheet. To drive real action, you need responsibility—with authority, accountability, and personal stakes. Learn how to move from passive documentation to active risk mitigation using data-driven assignment.
December 17, 2025
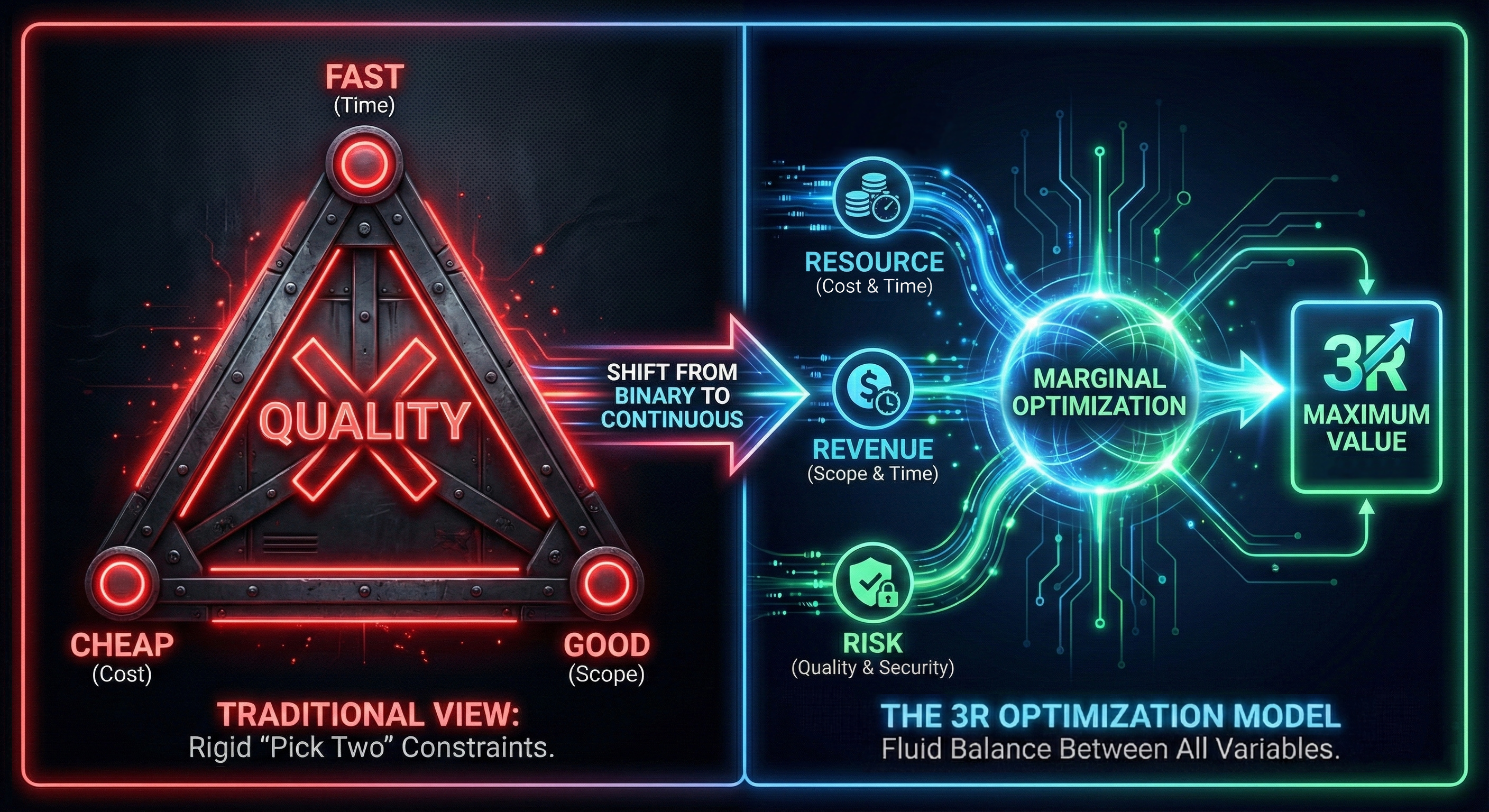
Why 'Fast, Cheap, Good—Pick Two' Is Wrong
The Iron Triangle says pick two. It's mathematically incorrect. The 3R Model—Revenue, Resources, Risk—shows how to optimize all three using marginal analysis.
September 27, 2025
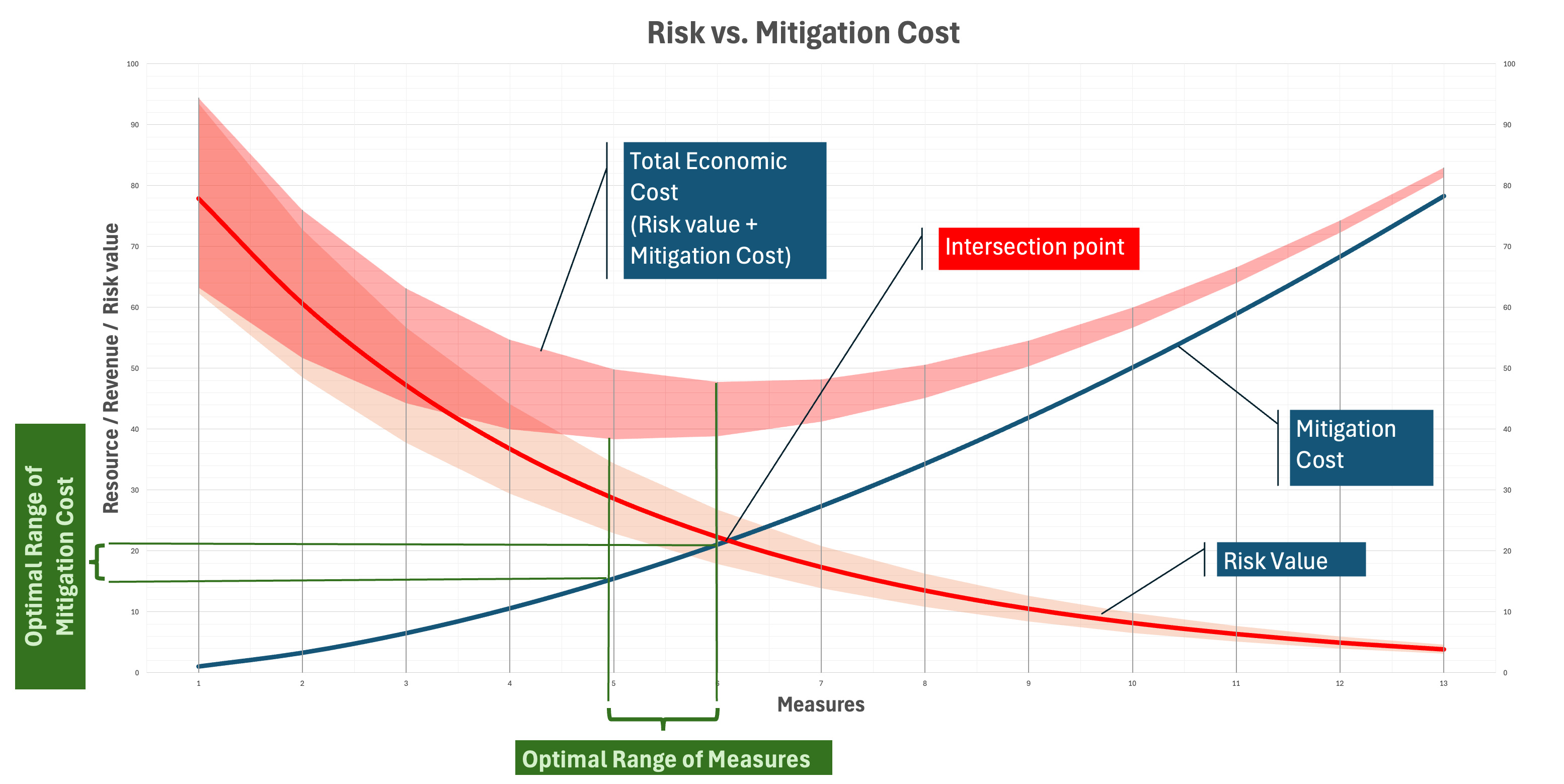
The Three R Framework: Optimizing Security Spend
The optimal point isn't where cost equals risk—it's where each dollar spent reduces risk by exactly one dollar. A practical guide to security economics.
September 27, 2025
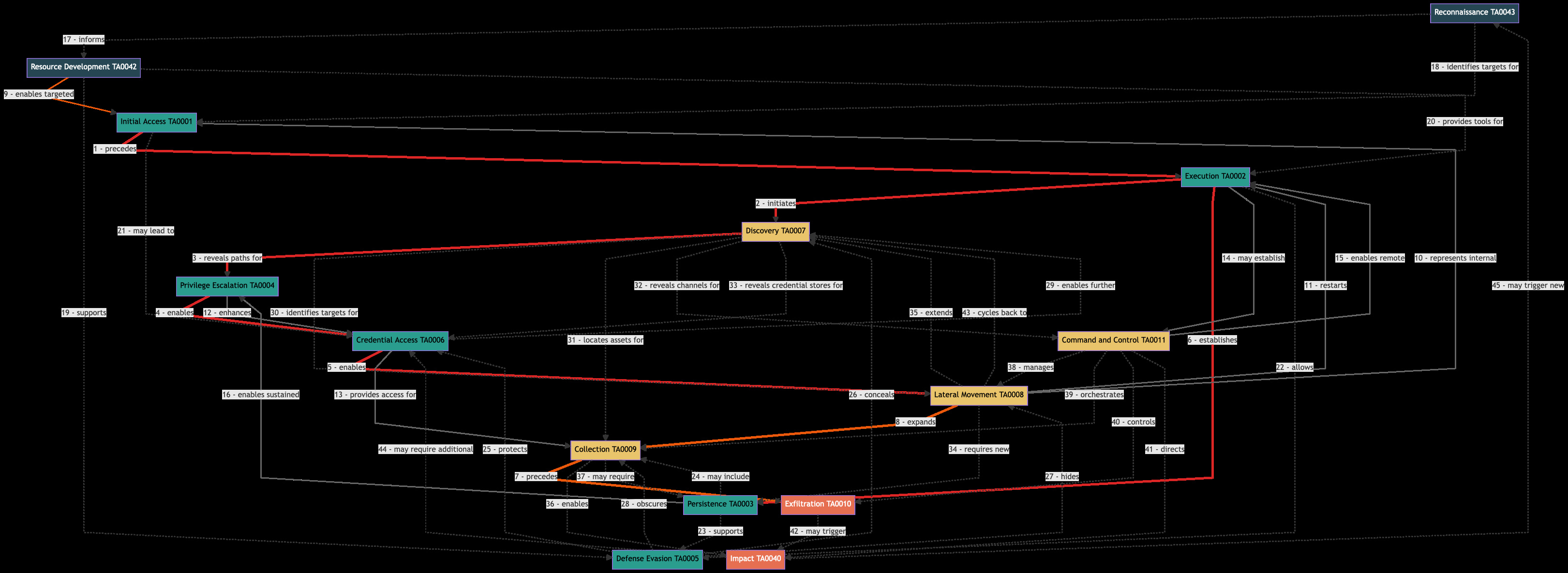
Beyond Kill Chains: A Graph-Theoretic Framework for Attack Modeling
This article proposes a graph-theoretic framework where attack tactics form nodes in a directed graph with weighted edges representing transition probabilities and dependencies.
September 25, 2025
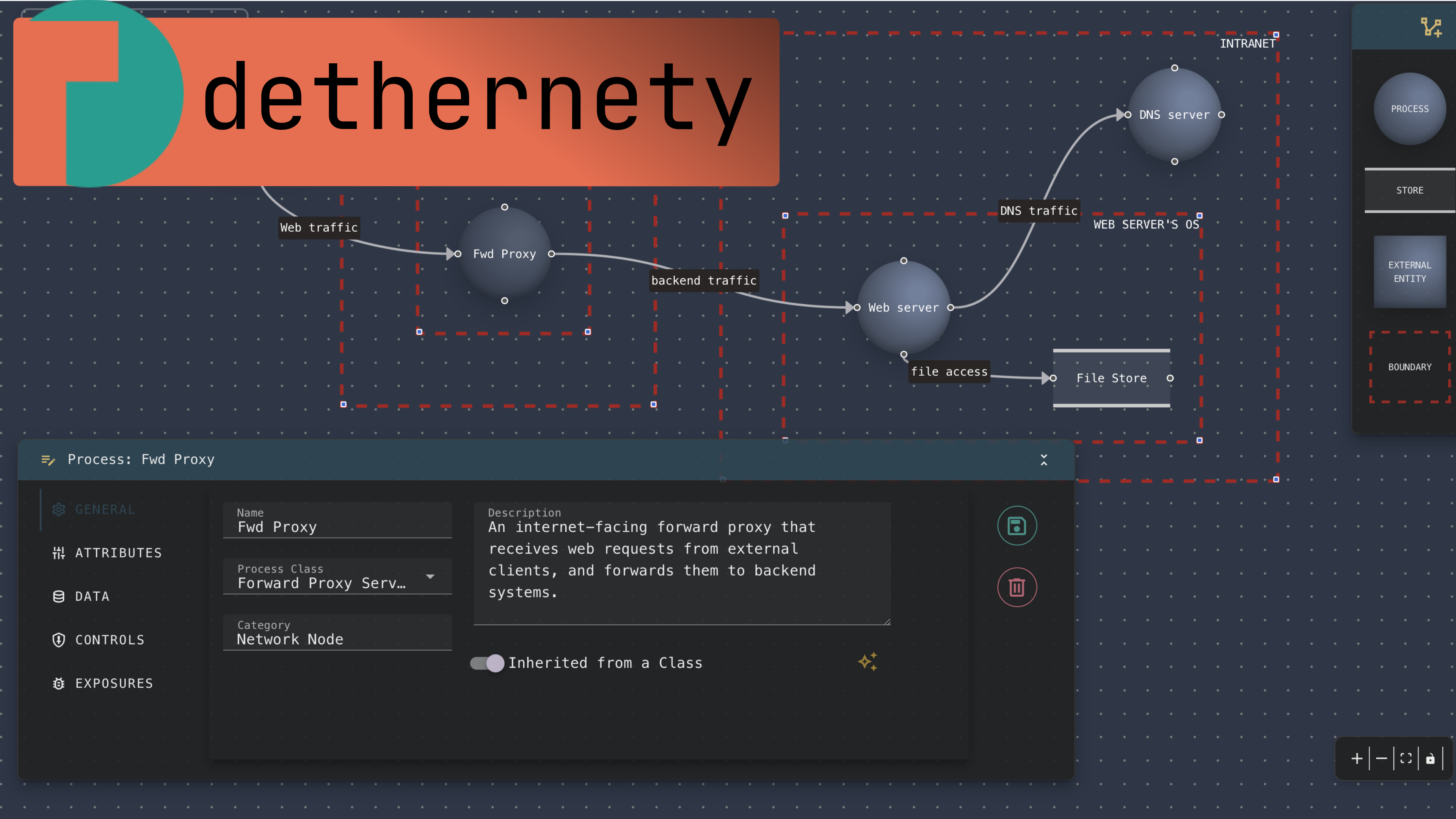
Announcing Dethernety: AI-Integrated Cybersecurity Threat Modeling
Introducing Dethernety, a revolutionary AI-powered threat modeling platform that helps organizations identify and mitigate security risks early in the development lifecycle.
September 20, 2025
