The Platform
Graph-native threat modeling with pluggable AI analytics, MITRE ATT&CK & D3FEND integration, and an extensible module ecosystem.
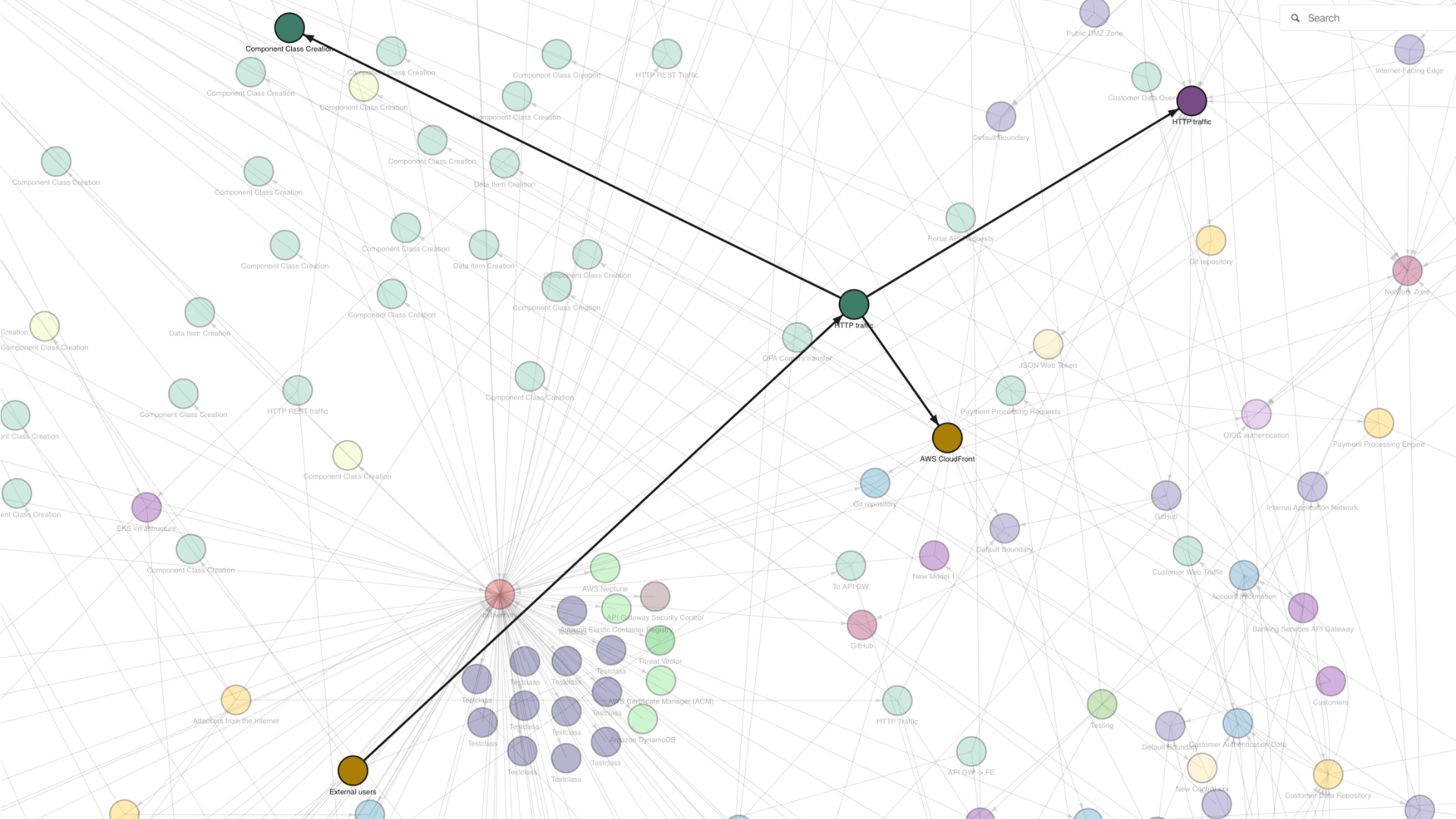
Graph-Native Foundation
Neo4j / Memgraph
Security relationships are first-class citizens, not JOIN operations. Attack paths, data flows, and escalation chains are stored as graph edges. Multi-hop analysis that would take hundreds of lines of SQL becomes a 4-line Cypher query.
- Relationships visible by default
- Real-time attack path traversal
- Cross-model graph queries
MITRE ATT&CK & D3FEND
Built-in, not bolted on
Exposures automatically map to ATT&CK techniques. Controls map to D3FEND countermeasures. Coverage gap analysis reveals which techniques are exposed and which controls address which threats.
- Automatic exposure-to-ATT&CK mapping
- Control-to-D3FEND countermeasures
- Coverage gap analysis in seconds
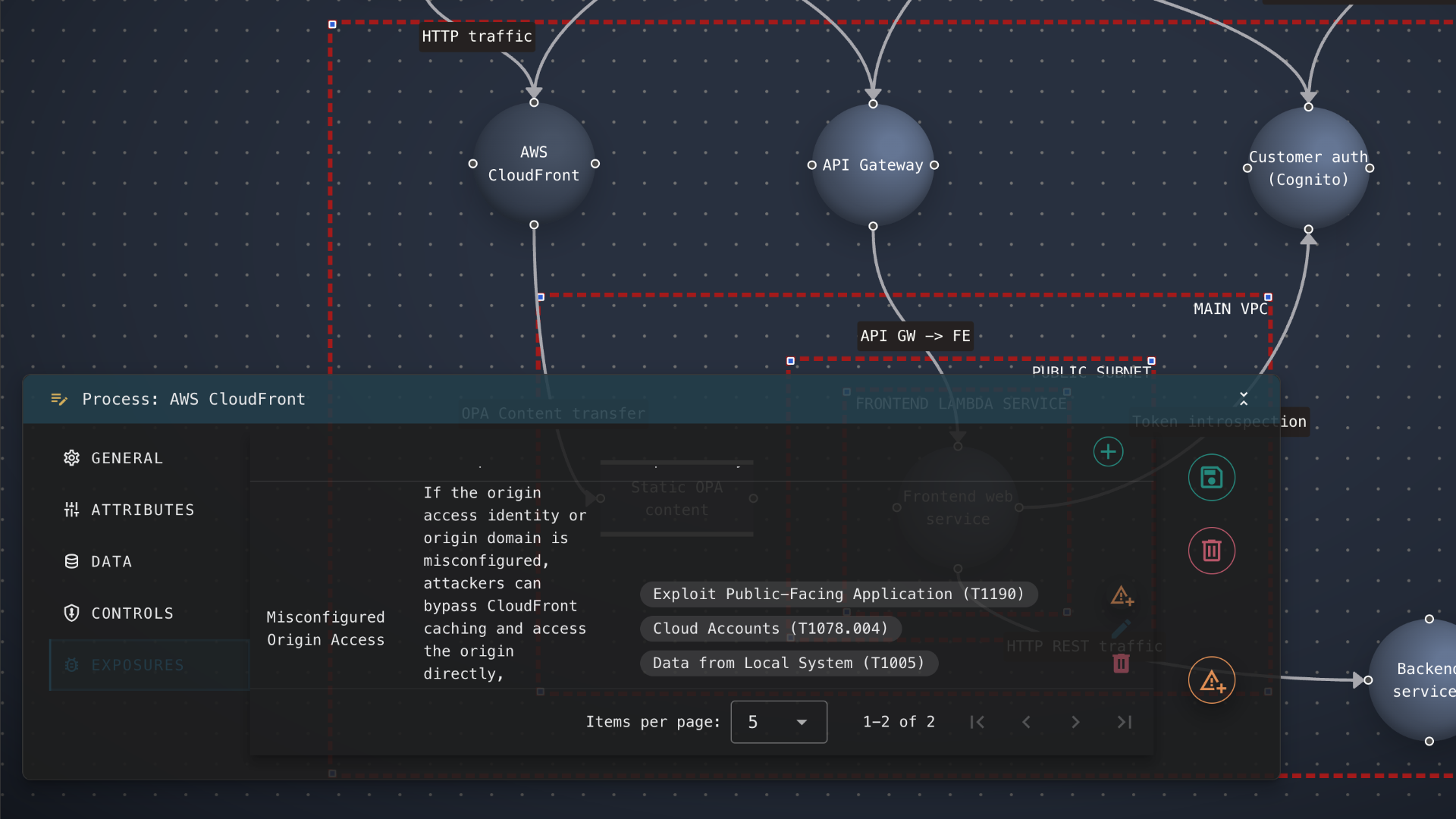
Module Ecosystem
Real plugins, not templates
JavaScript/TypeScript packages loaded at runtime. Design classes define component types with attributes and policies. Analysis classes create custom engines. Issue classes integrate with external trackers.
- Design, Analysis, and Issue classes
- OPA/Rego policy engine
- AI-assisted module creation via Studio
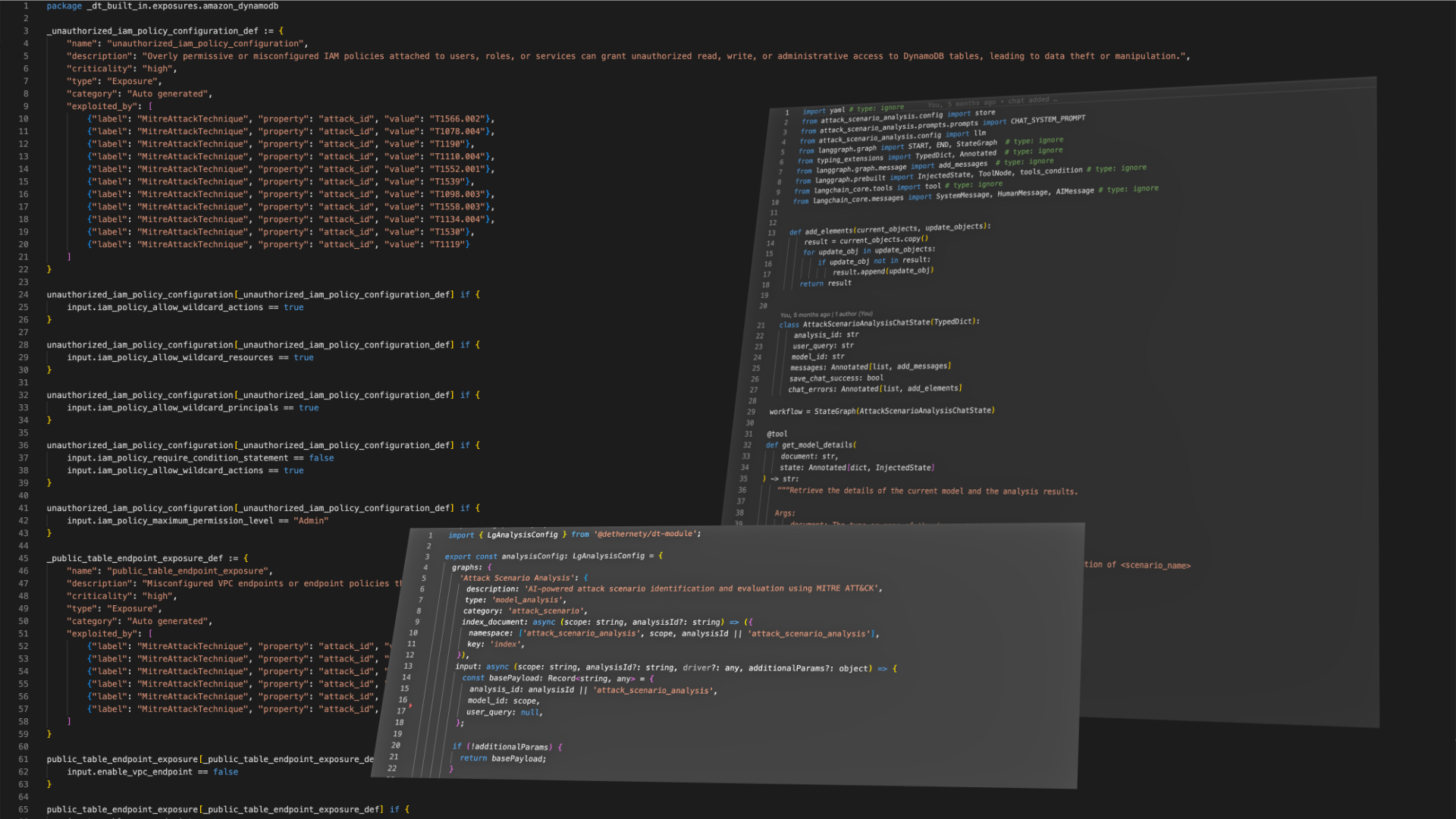
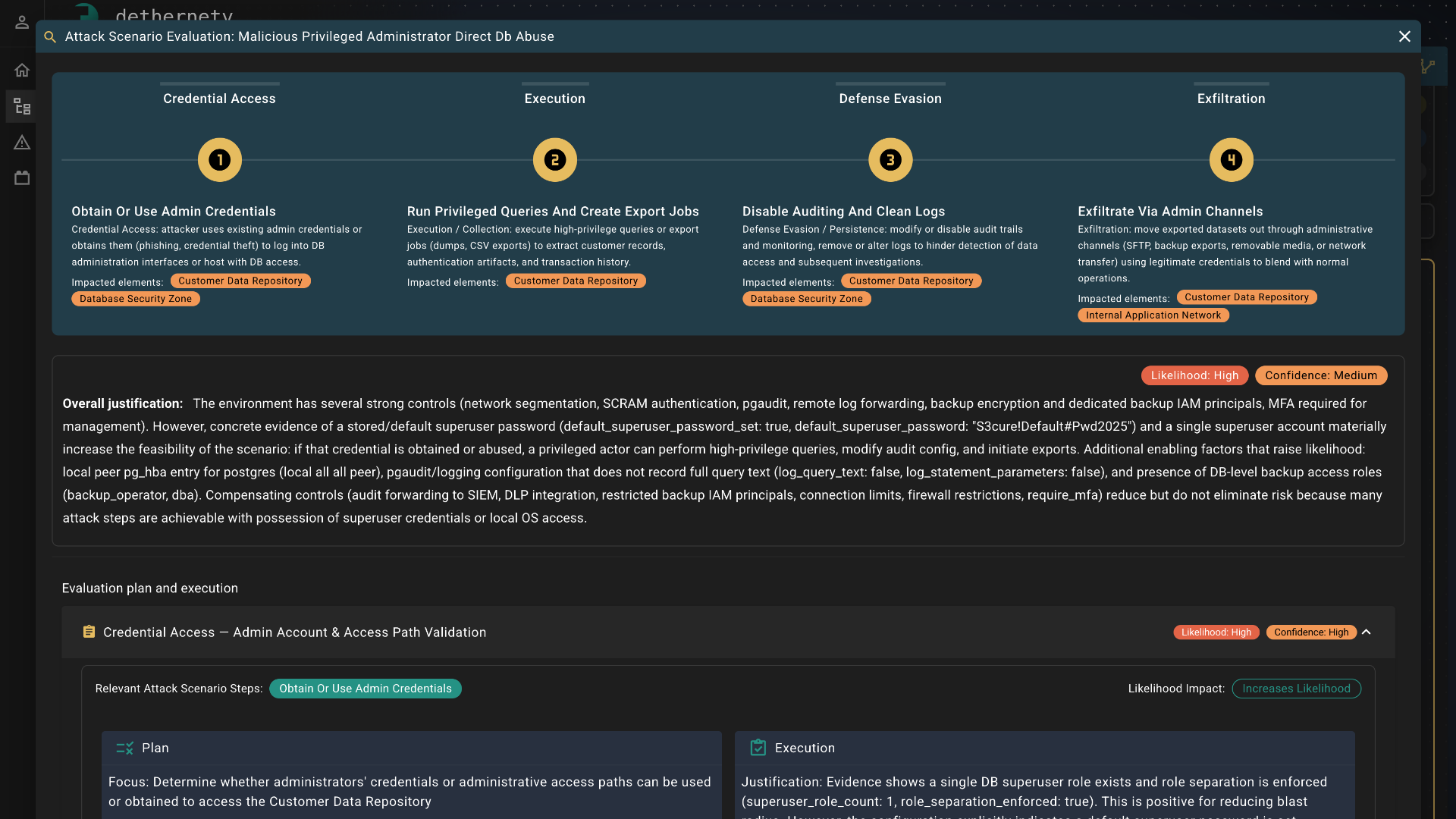
Pluggable Analysis
Context-aware, not component-only
Analysis sees the complete architecture graph, not isolated components. Choose from query-based deterministic analysis, single-agent AI acceleration, or multi-agent LangGraph workflows.
- Full model context analysis
- Swappable analysis engines
- Zero AI vendor lock-in
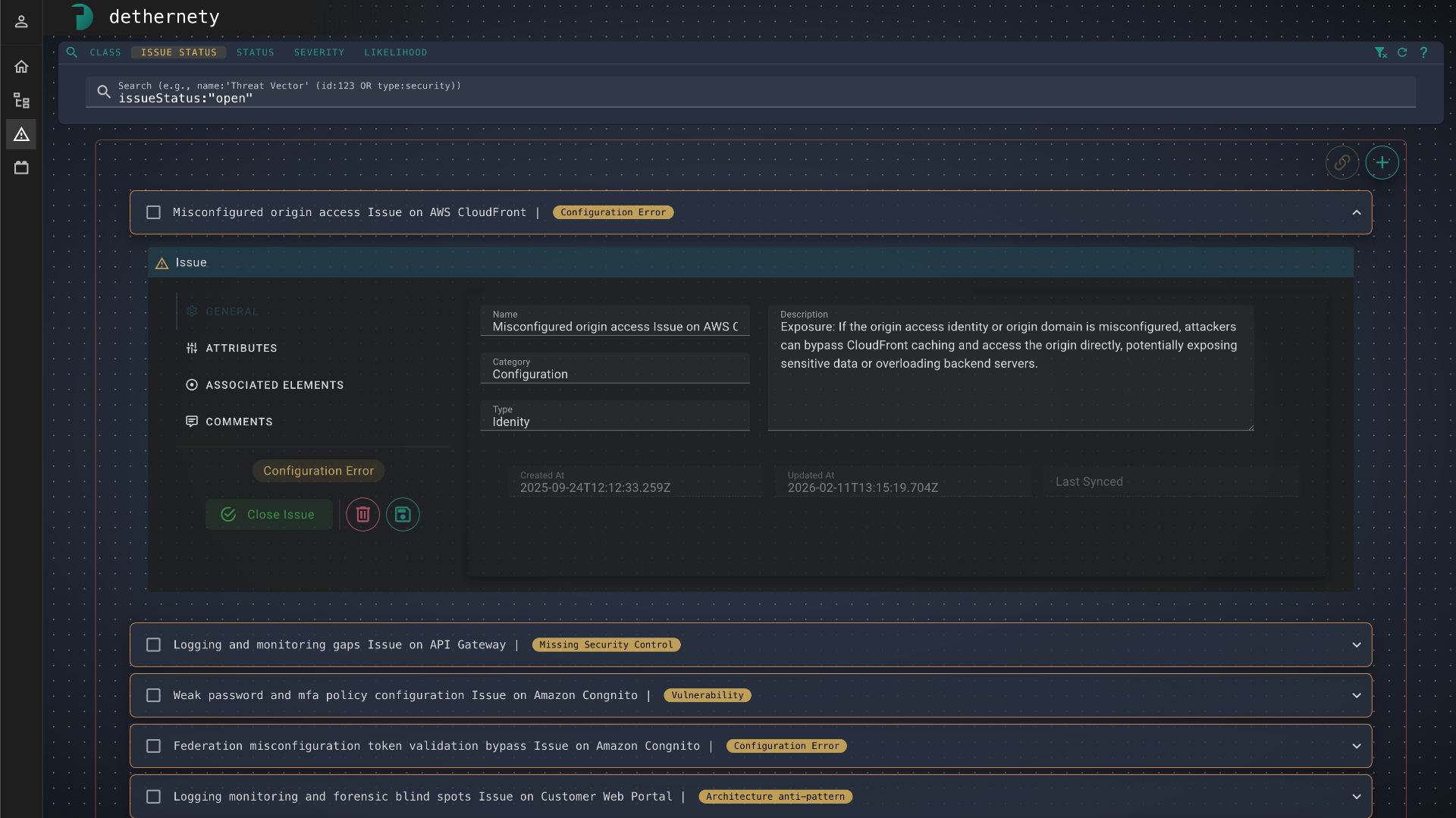
Issue Management
From finding to fix
Create actionable issues directly from analysis findings. Track remediation progress, assign ownership, and sync bidirectionally with external trackers through issue modules.
- One-click issue creation from findings
- Any tracker via issue modules
- Remediation tracking dashboard
One platform, multiple interfaces
Same graph database, same MITRE integration, same module ecosystem. Different workflows for different teams.
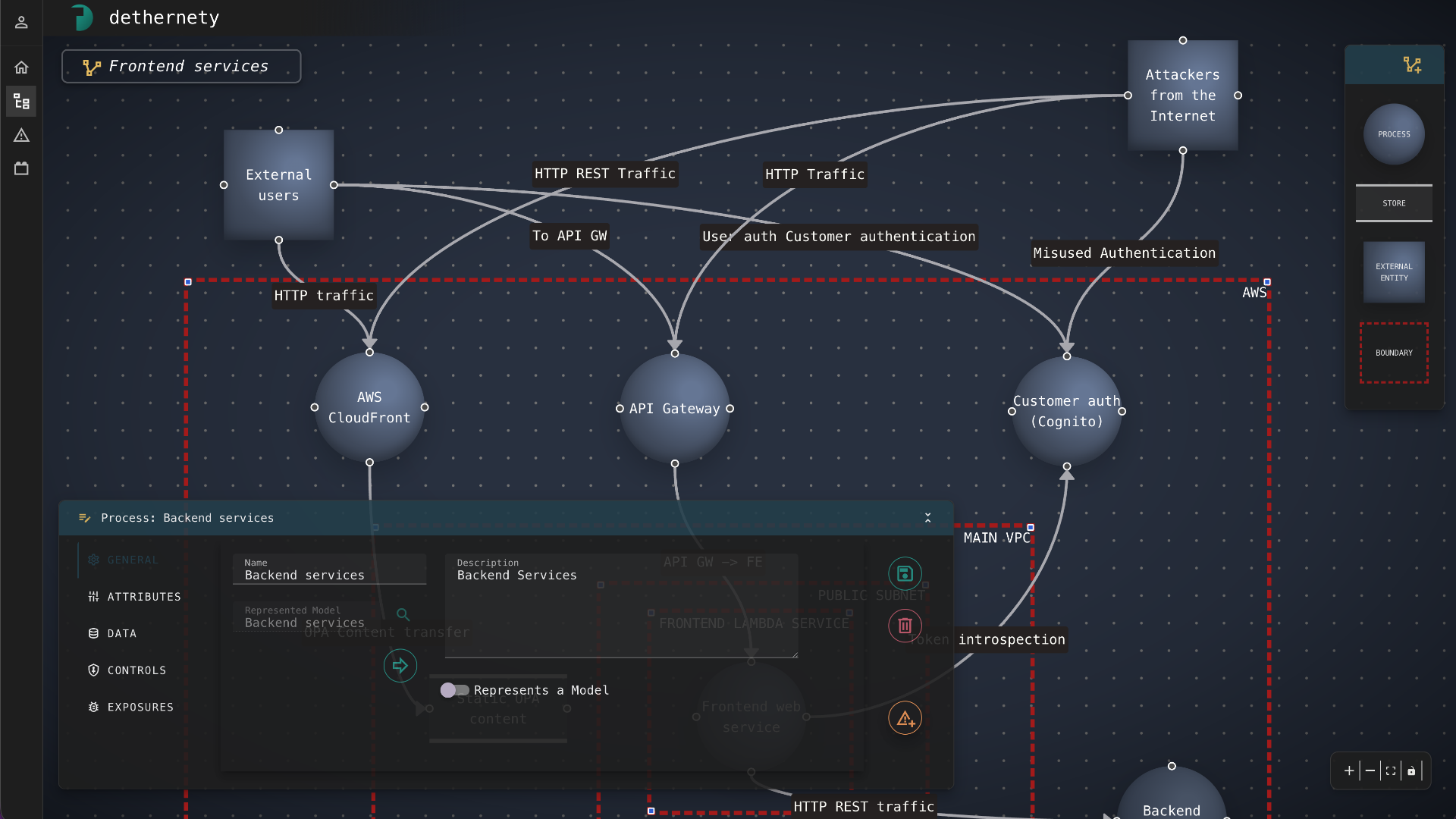
GUI
Security teams
Visual drag-and-drop threat modeling for security architects and compliance teams.
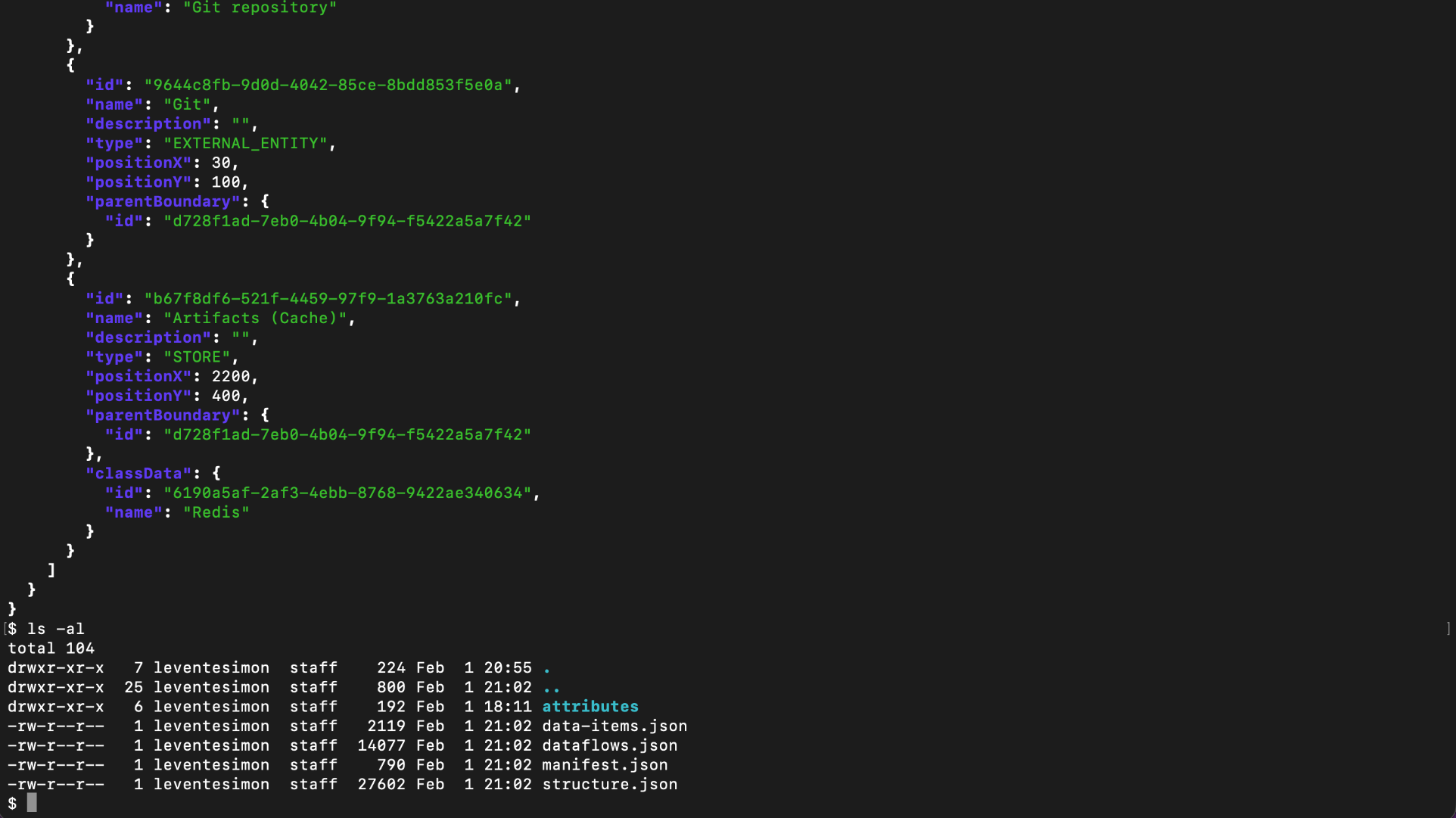
CLI
DevOps teams
Command-line automation for CI/CD pipelines. Threat-model-as-code with version control.
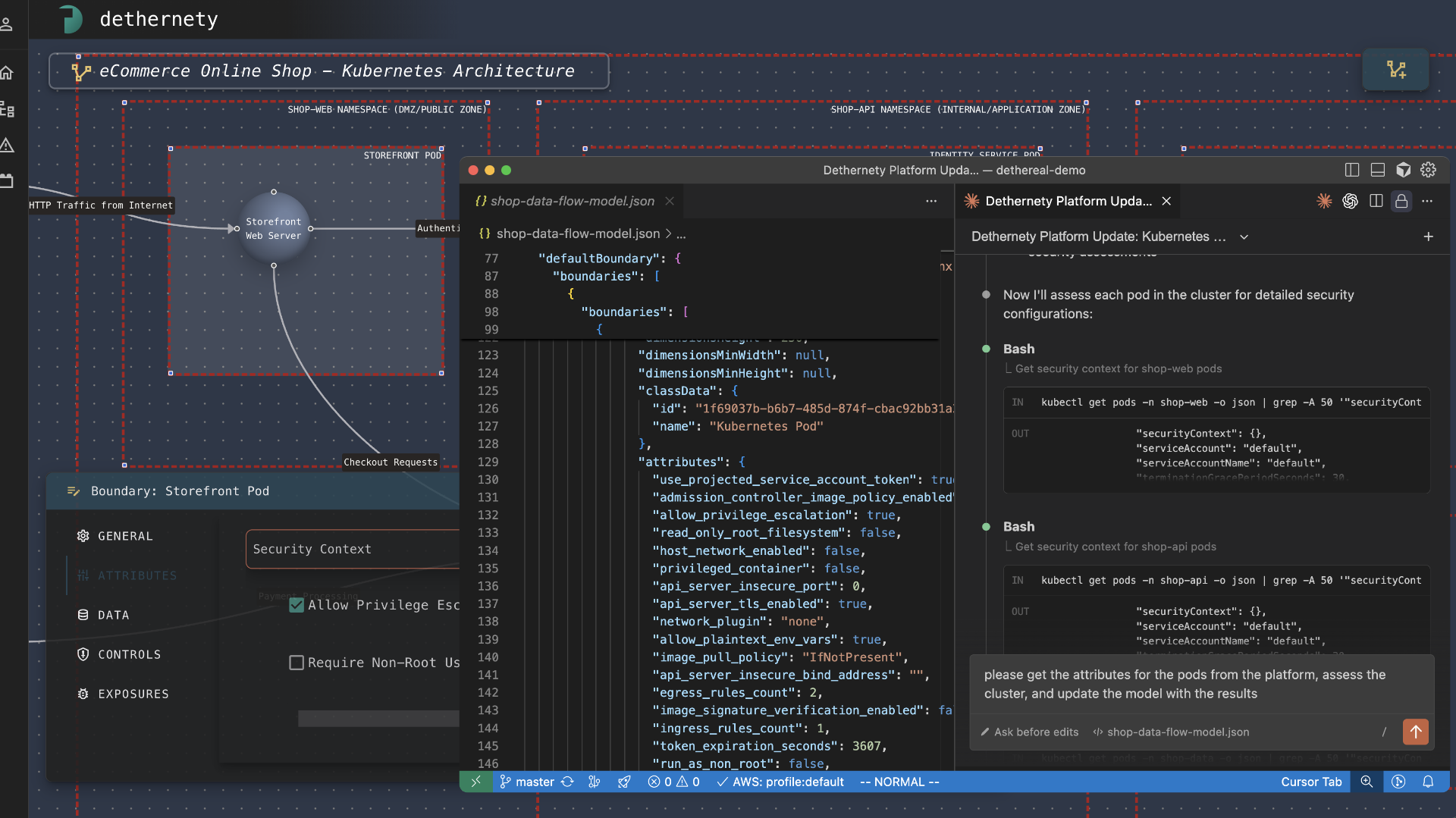
MCP
AI-assisted workflows
Model Context Protocol for AI agents. Conversational threat modeling and infrastructure discovery.
Infrastructure without compromise
SaaS speed with sovereign control. The same containerized stack deploys to cloud or air-gapped environments.
Blast Radius Isolation
Each customer gets a dedicated, isolated subnet and compute environment. A compromise of one customer is contained.
Immutable Infrastructure
Container-optimized OS with no patching. Entire instances are replaced, ensuring pristine state with no configuration drift.
Zero-Trust Access
Triple request validation with DNS hijacking prevention and isolated internal routing. Every hop is validated.
See it in action
Watch the platform demo or get in touch to discuss your threat modeling needs.